Green Screens Terminal service is based on WebSockets and JSON mapped remote callable statements which can be used not only by the web browser itself, but also by Node.JS, Go, and many more backend systems.
Want it or not, we needed to use WebSockets instead of standard REST simply because of a terminal protocol which requires full-duplex communication. That created additional demands in software structure, API design and the whole process in common.
One of such demands was security. When a request for a connection is created, it is in the form of encrypted URL parameters which also might contain user login data. To protect login data, we added many security measures for interactive online sessions.
In the beginning, extra online protection was based on IP, OTP and recently on FIDO2 standards to control access to the web resources.
However, resource protected by FIDO2 cannot be used in backend as they require user interaction. So, IP and OTP access controls are the only URL resource protection.
If IP access control is used, the problem is IP address of the connecting computer might change making encrypted URL unusable.
Along OTP, additional methods are also used to improve security which does fit very well in browser environment, but not when used in backend.
Thus, we introduced API Keys with latest 3.7.1 release.
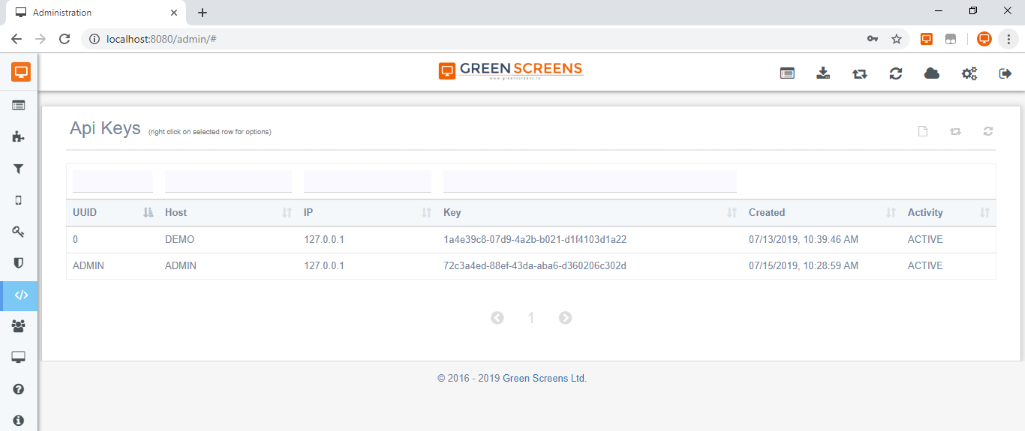
The question is how API Keys work?
API Keys turns off some browser specific security measures making encrypted access URLs insecure. Insecure in a mean of location access and access control (not data decryption). To prevent that, API keys are linked to the caller IP and such encrypted URL can be used only from a specific computer. API Keys are a mean of IP address virtualization. Disabling API Key instead of blocking IP address is a much better and more robust approach.
What all that means?
When using OTP or FIDO2, admins and users does not have to worry about encrypted session requests as they are generated automatically with all what is needed for safe access. In the opposite, when API Keys are used, the generated encrypted URL must be created manually and handed over to the user or API caller. Green Screen Terminal Service will validate client IP and API Key from received request with API Key internally saved on the server itself.
The First option is used primary from web browser and our mobile app and not suitable for backend, or automated use. The Secondary option is intended for backend automated tasks, but it is also possible to use API Key based encrypted URL from the browser and a specific IP address that corresponds to the IP registered on the server side.
As mentioned, the IP address of the calling side might change and in many cases it is much easier to go to the Green Screens Admin console and change the API Key IP address than regenerating URL again and reconfiguring the remote client. To disable remote calls, it is enough to disable API Key through admin server and better than blocking IP address.
These changes required us to update URL encrypted generator tools. One can check them from our GitHub repository here...